With the introduction of Peer Malicious Event Detection (MED), File Collaboration's real-time engine can now be used to spot unwanted activity being executed on storage platforms by ransomware, viruses, malware, hackers, or rogue users. This new technology provides alerting capabilities, as well as the ability to minimize the amount of encrypted or deleted content from being replicated to remote locations. For more information, visit https://kb.peersoftware.com/tb/introduction-to-peer-med.
Peer MED deploys three different mechanisms for spotting malicious activity, each of which can be enabled and tuned independently. These settings are configured on a global level. Once MED is enabled and jobs are restarted, these capabilities will apply to all jobs. To view and modify these settings, click on the Window menu from with the Peer Management Center, and select Preferences. On the left-hand side of the dialog that pops up, open the tree node titled Real-time Detection and select MED Configuration. The following screen will be displayed.
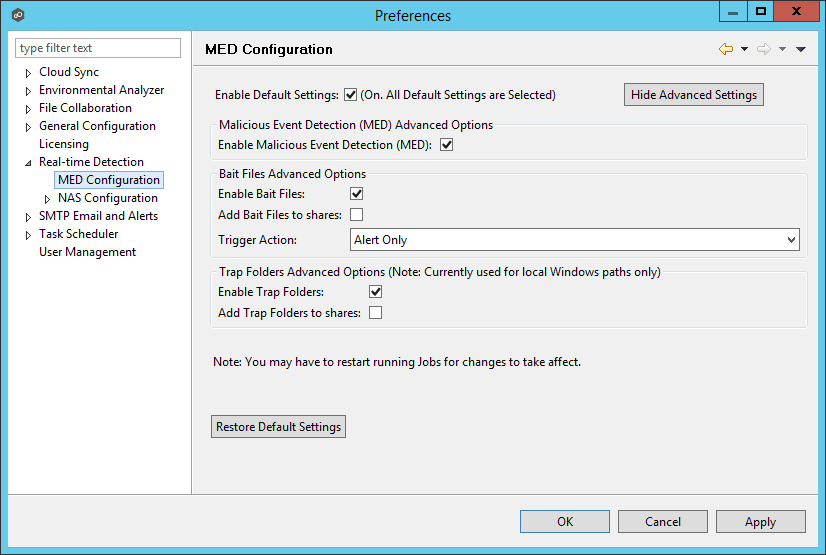
The main options are as follows:
Enable Default Settings |
Enables/disables Peer MED using default settings. By default, all three MED mechanisms are enabled. |
Show/Hide Advanced Settings |
Shows/hides options for each of the three MED mechanisms. |
Enable Malicious Event Detection (MED) |
The master on/off switch for MED. If unchecked, all MED mechanisms will be disabled. |
Restore Default Settings |
Restores all defaults across the three MED mechanisms. |
Bait Files
Bait files are files of common types, inserted into the file system in a way that hides them from users. Though hidden, these bait files are likely to be accessed by automated processes (like ransomware) or by mass deletions of entire folder structures. As soon as these files are touched, an action is triggered.
The options for Bait Files are:
Enable Bait Files |
Enables/Disables bait file creation and monitoring. |
Add Bait Files to shares |
At the start of each job, create bait files under the root of each participant's configured watch directory. To see the watch directory for a job, review Host Participants and Directories. |
Trigger Action |
Defines the action to take when MED detects malicious activity on a bait file. See below for more details on available actions. |
Trap Folders
On Windows File Servers, Peer MED can be configured to create hidden recursive folders that attempt to trap or slowdown ransomware as it enumerates a folder structure. As with the bait files, these folders cannot be seen by users but will be accessible by automated processes. If bait files (above) are enabled, a bait file will be placed within each trap folder, and an action will be triggered as soon as these files are touched.
Options for trap folders are:
Enable Trap Folders |
Enables/disables the creation and monitoring of trap folders. |
Add Trap Folders to shares |
At the start of each job, create trap folders under the root of each participant's configured watch directory. To see the watch directory for a job, review Host Participants and Directories. Note: Trap Folders will only be used with participants that are Windows File Servers. As such, these settings will not apply to any other enterprise NAS device. |
Action Types
For each MED mechanism, one of four actions can be configured on the detection of malicious activity. These actions are:
Alert Only |
Triggers an alert in the Peer Management Center. If SMTP email alerts are configured for MED Alerts and enabled for a job, an email will also be sent. For details on SMTP email alerts, see Global Email options. If SNMP traps are configured for MED Alerts and enabled for a job, an SNMP trap will also be sent. For more details on SNMP, see Global SNMP options. |
Alert and Disable Host |
Triggers an alert while also removing the afflicted Agent from the job in which the malicious activity was detected. Once disabled, Agents will need to be manually re-enabled for collaboration to resume. |
Alert and Stop Job |
Triggers an alert while also stopping the job where the malicious activity was detected. Jobs will need to be restarted in order for collaboration to resume. |
Alert, Disable Host and Stop Job |
Triggers an alert, removes the afflicted Agent from the job where the malicious activity was detected, AND stops this job. This option is the most aggressive and will require administrators to re-enable Agents as well as restart jobs. |
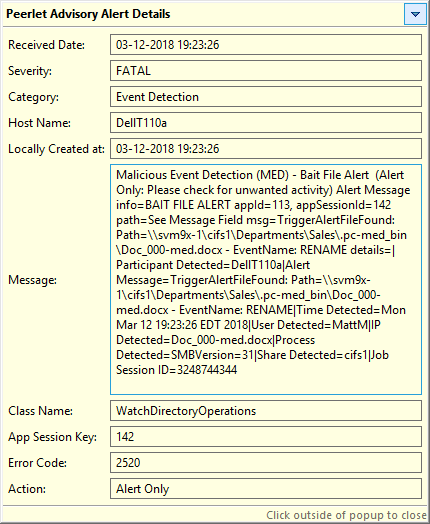
An example of an alert as displayed in the Peer Management Center is as follows:
Re-enabling a Disabled Agent Within a Job
Once disabled within a collaboration job, an Agent will not be involved in replication or locking. After the malicious activity that triggered MED is investigated and it is safe to bring the afflicted Agent back into collaboration, it will need to be re-enabled on a per job basis. To review the status of an Agent within a job and to re-enable it, navigate to the Participants View of the job.
If an error is disabled because of a MED action, it will look like the following:
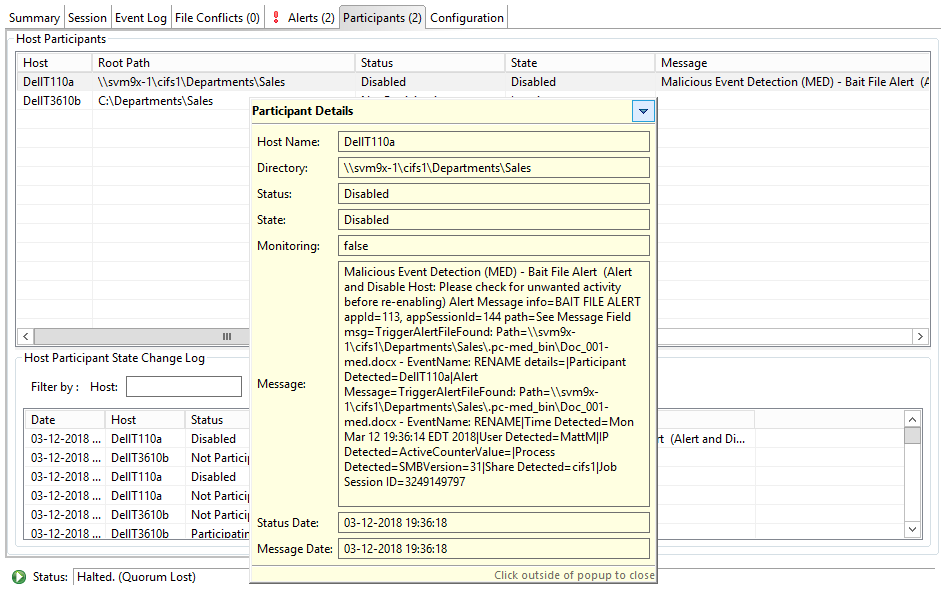
To re-enable the Agent, right click it within this view, and select Enable Host Participant.