This step is optional.
The File Metadata page allows you to specify whether you want to replicate NTFS security permissions metadata and the types of metadata to synchronize. It also allows you to specify which volume/share/folder's metadata should be used if there is a conflict during the initial synchronization. The volume/share/folder used if there is a conflict is referred to as the master host.
For more information on synchronizing NTFS metadata, see File Metadata Synchronization in the Advanced Topics section.
To enable file metadata synchronization:
1.Select when you want the metadata replicated (you can select one or both options):
•Enable synchronizing NTFS security descriptors (ACLs) in real-time - Select this option if you want the metadata synchronized in real-time. If enabled, changes to the selected security descriptor components (Owner, DACL, and SACL) will be transferred to the target host file(s) as they occur.
•Enable synchronizing NTFS security descriptors (ACLs) with master host during initial scan - Select this option if you want the metadata replicated during the initial scan. If enabled, changes to the selected security descriptor components (Owner, DACL, and SACL) will be synchronized during the initial scan.
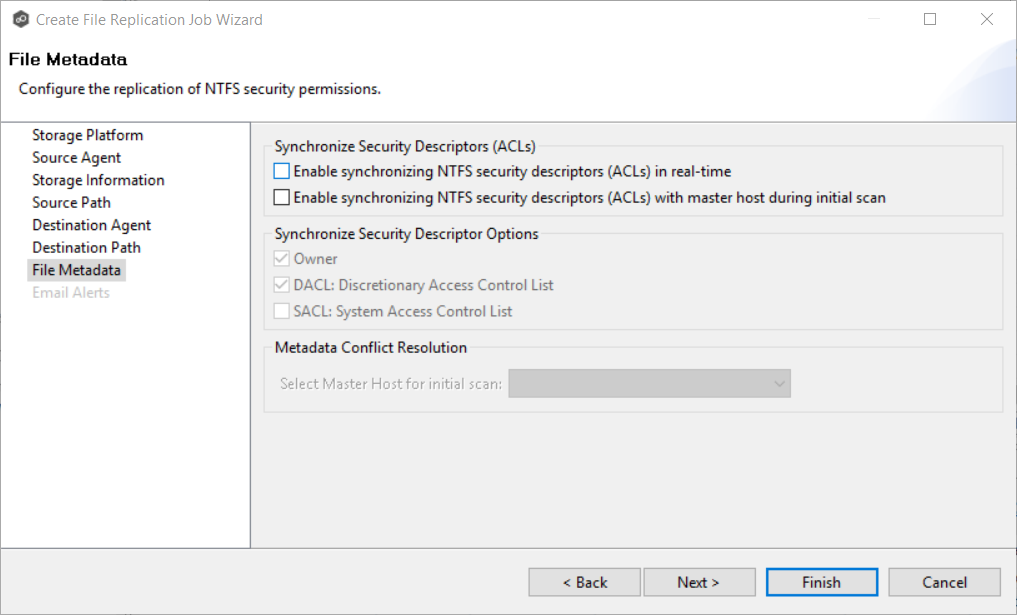
2.Click OK in the message that appears after selecting a metadata option.
3.If you selected either of the first two options in the Synchronize Security Descriptor Options section, select the security descriptor components (Owner, DACL, and SACL) to be synchronized.
4.If you selected the option for metadata synchronization during the initial scan, select the host to be used as the master host in case of file metadata conflict.
If a master host is not selected, then no metadata synchronization will be performed during the initial scan. If one or more security descriptors do not match across participants during the initial scan, conflict resolution will use permissions from the designated master host as the winner. If the file does not exist on the designated master host, a winner will be randomly picked from the other participants.
5.Click Next.
The Email Alerts page is displayed.